Home Hi-Tech Hardware and Peripherals ,,,,, Secure-K is a USB key created by Mon-K data protection, an Italian-English company (offices in London and Milan) born in 2013 and whose mission is security and privacy. The USB stick in question integrates hardware and software encryption functionality. The device is a little longer than the keys that we are used to seeing around but it is light, pocket-sized and comes in a curious cylindrical package. Inside this we find a leaflet with the basic instructions and the actual key with a USB 3 connector at the end and a mini keyboard on the casing for typing the access code.
 The packaging
The packaging
Unblocking procedure The first operation to be carried out is to enter the 8-digit PIN (a code of up to 15 digits can be set) which allows the unlocking of the Secure- K and recognition on the host computer. Nothing will happen when you plug the device into a USB port; in order for it to be recognized, it must be unlocked: press (on the pen) once the key with the symbol of a key.
The three LEDs flash together and the left LED (red) starts flashing; within ten seconds you must enter the unlock PIN code (by default 11223344); by pressing the key symbol again, the green LED lights up to indicate that Secure-k is ready to be activated on the host computer. The key can now be used like any other USB key or disk.
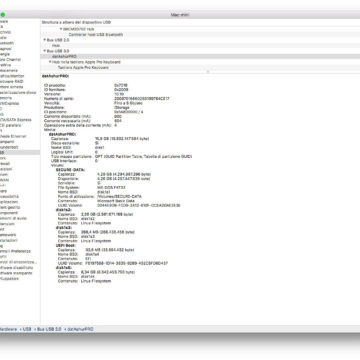 Details on the Secure-K key from macOS System Profiler
Details on the Secure-K key from macOS System Profiler  External view
External view  External view
External view  The package
The package  The keyboard for entering the unlock codes
The keyboard for entering the unlock codes  Detail of the package
Detail of the package  Detail of the package
Detail of the package 
 The package in which the key arrives
The package in which the key arrives
Encryption The device integrates various technologies and it is wrong to consider it only a stick: it is based on Linux and according to the manufacturer it was created to offer features that take into account security, privacy and reliability . The peculiarities of the product make it suitable for use in complex and structured enterprise environments; the user can use the system to take his work with him: in case of problems, he can remain relatively calm thanks to the protection of the code.
Security is guaranteed by the FIPS 140-2 military standard (double encryption with release and anti-tampering system). The manufacturer guarantees that the device is protected from external attacks thanks to the 256-bit AES encryption and from internal ones thanks to the 512-bit AES software encryption. Host segregation (2-way protection), backup and restore (for data recovery and setting) are provided. The security mechanism provides for the deletion of data after 10 failed access attempts.
Secure-K, as a “closed” system, has an encrypted data exchange partition, readable only by the operating system that has read the key as “unlocked”. The Enterprise version is optimized to work in a structured and complex business environment, taking into account various Microsoft technologies, all in compliance with the company's security and compliance policies.
 The keyboard for entering the unlock codes
The keyboard for entering the unlock codes
The integrated operating system As we have already mentioned, Secure-K is not just a stick. On this there is a partition with an operating system (“Secure-K OS”) that can be used to boot most Macs or PCs with an Intel processor. After having opened the device with the system seen before, just leave it inserted in the computer and restart it from the key (on Mac just hold down the Alt key at startup and start the system on the USB disk).
From the integrated operating system, after typing in the username and password (the default ones are shown in the leaflet attached to the product packaging), it is possible to recall various applications and software (which can be used directly from the key), print and use applications in full compliance with the stringent security rules envisaged in data centers.
The operating system provides a file manager, backup & restore functions, applications for anonymous web browsing, a chat for encrypted audio and video communications. The hidden partition with the operating system is not writable but it is possible to perform a complete system update, updating both the applications and the kernel. There is a data exchange partition not encrypted by software but protected by hardware encryption to facilitate data exchange on already started computers. In case of accidental loss, it is also possible to activate the “remote wiping” function to remotely delete the content as soon as the system is connected to the internet.
The product is designed for the Enterprise sector and arrives on the market with only one model available at the hardware level with the possibility of customizing the software part ad hoc according to the needs of the company. The available variants are: 8GB, 16GB, 32GB and 64GB. In Italy the product is distributed by CREAplus but the manufacturer has other partners in Italy, one also in Saudi Arabia. List prices start at € 199.00 for the 8GB version (price including subscription for Sync & share features). More details and specific offers for companies on the manufacturer's website.
Pro
Cons
,,





